
The ninth edition of the ENISA Threat Landscape (ETL) report released in October 2021 discusses a list of prime cybersecurity threats affecting the European Union. The Internet has no borders and such threats are not particularly unique to the EU. It is good, however, to follow the trends and identify security solutions that help organizations tackle these threats.
In this blog post we will look at each one of them and how DRACOON can help to solve them.
https://www.consilium.europa.eu/en/infographics/cyber-threats-eu/
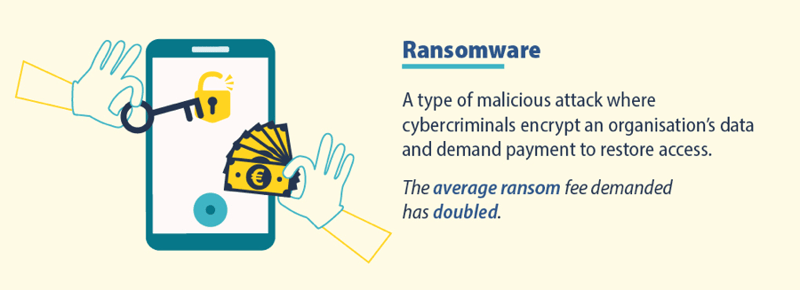
According to the study, financial damage due to ransomware has more than doubled. This demonstrates that private organizations and the public sector are still not able to tackle such class of attack. The main reason for this is that, while an attack is very simple to execute, building up defenses is very hard. Organizations still struggle to find the balance between productivity and security, with the latter usually falling short.
With DRACOON, all your files are backed up multiple times. A technique called “versioning” allows users to roll back previous versions of the same file, which is an immediate solution against ransomware.

https://www.consilium.europa.eu/en/infographics/cyber-threats-eu/
Since the beginning of the computer interconnectivity, computer viruses were always at the forefront of the malicious space in the digital world. As an evolution to that, malware still make the news even though anti-virus technology has improved significantly.
One of the ways to prevent malware to spread is to detect malicious files early in the infection cycle. With an integration with G-Data, files in DRACOON are scanned against malware and prevents malicious content from spreading through the network. More information on G-Data will follow shortly.
https://www.consilium.europa.eu/en/infographics/cyber-threats-eu/
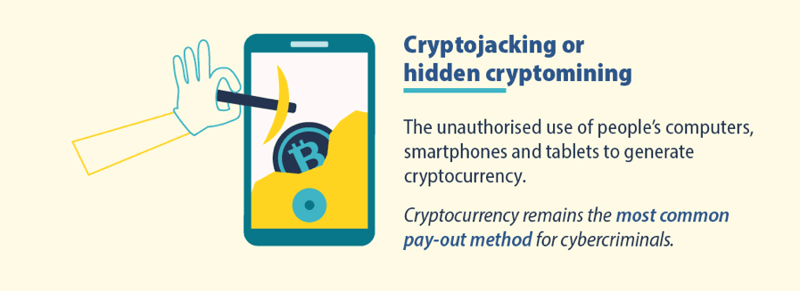
The study also suggests that cryptocurrency is the most common payment method used by cybercriminals. A common attack is to compromise poorly managed servers, where cybercriminals can mine cryptocurrency and profit from it while the victim organization pays the bill.
DRACOON provides a cloud solution for end-to-end encrypted file and data exchange platform. Customers have full control of their data while DRACOON takes care of the rest.

https://www.consilium.europa.eu/en/infographics/cyber-threats-eu/
There is a reason why people send files as attachments to email. It’s easy and it works. But this also brings a number of security challenges, such as malicious attachments and loss of control of the file.
With DRACOON, users can easily send files via email by creating a share-link, which gives the recipient access to the information and the sender has full control of the data. This is made even easier with the Microsoft Outlook Add-In, which automatically transforms attachments into DRACOON share-links.
https://www.consilium.europa.eu/en/infographics/cyber-threats-eu/
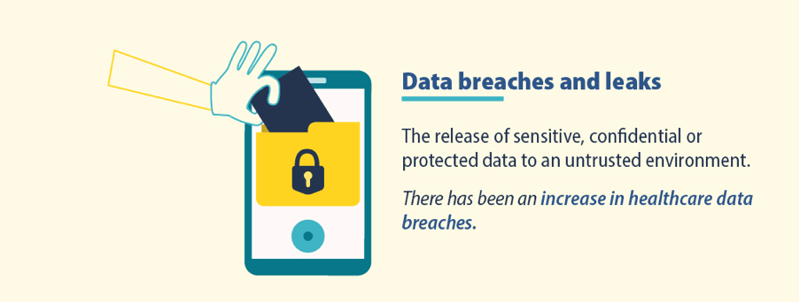
Regardless of data protection regulations like the GDPR, data leaks still regularly make the news. This not only affect the freedoms of the individual, who has personal data exposed to unknown adversaries, but also organizations with their intellectual property and trade secrets.
DRACOON provides a customizable system for data classification where rules can be enforced centrally, lowering the risk of human error or insider threats.
https://www.consilium.europa.eu/en/infographics/cyber-threats-eu/
Part of what constitutes the reputation of a company comes from how reliable their services are. Interruption of service also leads to financial damage when revenue is made by online transactions. For some, access to data is of paramount importance to deliver services.
DRACOON utilizes highly scalable infrastructure and network protections in order to keep customer data with high availability requirements. In preparation for the ISO 22301 certification, DRACOON also implements robust business continuity management processes for faster and reliable system recovery in case of disasters.

https://www.consilium.europa.eu/en/infographics/cyber-threats-eu/
The Internet brought information to the palm of our hands in a matter of seconds. Such technology marvel is good but is also used for nefarious purposes. With so much information available, it is difficult for the reader to verify its authenticity or its source.
With DRACOON, you control your data. Encryption technology ensures your data is secure and only visible by you. With a partnership with FP-Sign, files can be digitally signed in order to provide authenticity to the information being shared, giving comfort to the receiver that it comes from a reliable source.

https://www.consilium.europa.eu/en/infographics/cyber-threats-eu/
Managing IT infrastructure is not only expensive but also hard. User error and server misconfiguration are amongst the top security threats as reported by ENISA. The move to the cloud helped to mitigate some of this threat, where organizations can focus on the business and the cloud provider takes care of the underlying technology.
Using certified data centers in Germany, DRACOON provides a reliable and resilient cloud infrastructure that powers the file and data exchange platform. Server and services are hardened automatically using configuration technology based on CIS Benchmarks and other known security standards.
https://www.consilium.europa.eu/en/infographics/cyber-threats-eu/
The world is an interconnected mesh of products and services. In some cases, it is hard to identify which link of the chain may disrupt businesses.
That’s why DRACOON is certified against the highest security standards available such as the ISO 27001 and the BSI C5:2020. As a cloud provider, DRACOON provides full transparency about the security program and enables customers to decide how best to integrate DRACOON in their own technology stack and risk profiles.

In this section, we explain the most important terms once again and clarify crucial questions about the topic.
The term "cyber attack" refers to a targeted attack in virtual cyber space on one or more information technology systems with the aim of completely or partially impairing the affected IT systems.
Cybersecurity or IT security refers to the protection of computer systems, networks, robots or cyber-physical systems against damage to their hardware and software, against theft or the data they process, and against the misuse of services and functions or their disruption.
Malicious software used for the following purposes: Damage or disruption of a device or unauthorised intrusion into the device. Malware attacks have decreased by 43% in the EU.
The unauthorised use of people's computers, smartphones and tablets to generate cryptocurrencies. The use of cryptocurrencies remains the most common withdrawal method used by cybercriminals.
Attempts to steal passwords or credit card data through various techniques such as phishing, smishing and spam. Bait attempts related to COVID-19 continue to dominate email attack campaigns.
The disclosure of sensitive, confidential or protected data to an untrusted environment. There were more cases of health data misuse.
🔎 Distributed Denial of Service attacks (DDoS attacks)
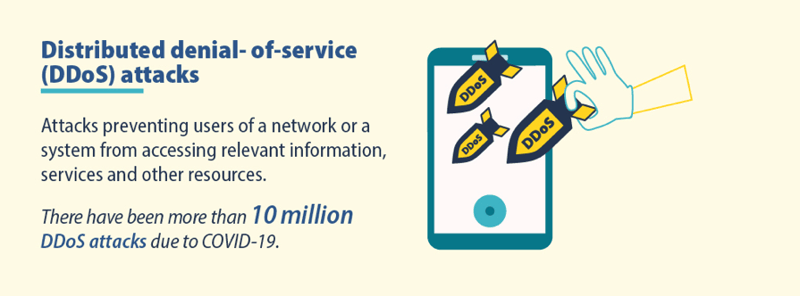
Attacks in which network or system users are prevented from accessing relevant information, services and other resources. As a result of COVID-19, there have been more than 10 million DDoS attacks.
Deliberate attack consisting of creating or passing on false and misleading information in order to manipulate public opinion. COVID-19 is one of the main targets for disinformation attacks.
These are mostly due to human error or physical damage to IT infrastructure. 50% of attacks are due to misconfiguration.
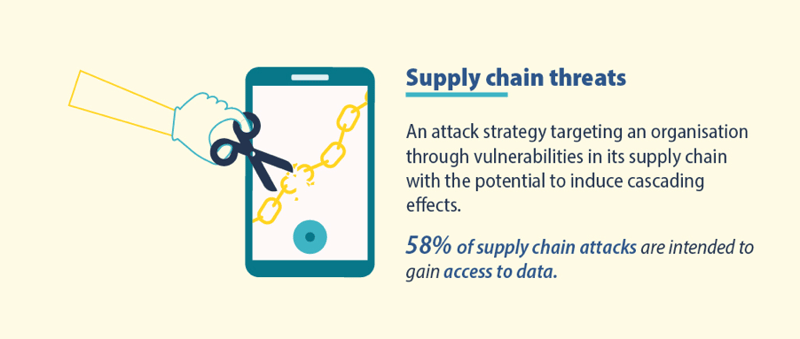
A strategy for attacking an organisation using vulnerabilities in its supply chain, which can cause cascading effects. 58% of attacks on supply chains are aimed at gaining access to data.
The Covid pandemic inevitably triggered a digital transformation in many companies. Within a very short period of time, companies were forced to send their employees to the home office. However, this demand for digital infrastructures also provided additional attack surfaces that hackers exploited to the full.
These Stories on Product & Features

© 2023 DRACOON GmbH
Made in Germany
Phone. +49 (941) 7 83 85-0